Security in IT can keep people awake at nights. There are many new services and features introduced to Azure every year. It is not easy to keep a track of everything as an administrator or even as a team. Sudden exploits at any level can cost organisations valuable money and thereafter their credibility. So how can we make sure our services on cloud are secure as best it can get?
This is answered with Azure Security Benchmark.
There are three main guidelines provide security standards.
- Center of Internet Security (CIS)
- National Institute of Standards and Technology (NIST)
- Payment Card Industry Data Security Standards (PCI - DSS)
Azure Security Benchmark assigns relevant combinations in each guidelines to 12 different control areas.
- Network Security (NS)
- Identity Management (IM)
- Privileged Access (PA)
- Data Protection (DP)
- Asset Management (AM)
- Logging and Threat Detection (LT)
- Incident Response (IR)
- Posture and Vulnerability Management (PV)
- Endpoint Security (ES)
- Backup and Recovery (BR)
- DevOps Security (DS)
- Governance and Strategy (GS)
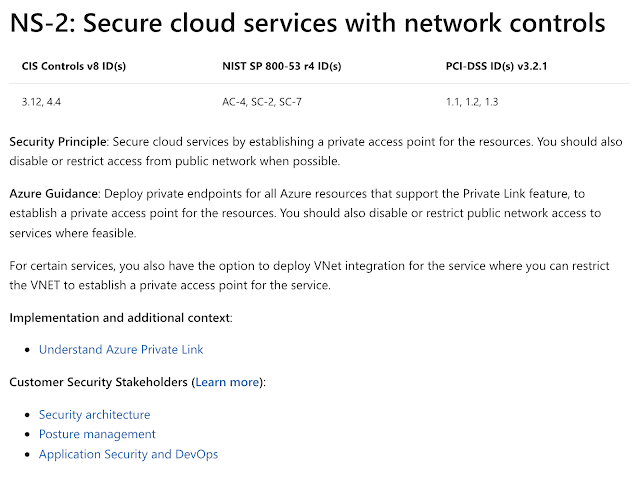
Inside each control area, there is a list of recommendations with each having a Benchmark ID and more information as shown in the image below. Source: docs.microsoft.com
Then each service is mapped to the necessary recommendations applicable to each control.
Eg: Cosmos DB can be implemented with following Network Security recommendations.
NS-1, NS-2, NS-3, NS-4, NS-6, NS-7
The there are following Identity Management recommendations.
IM-1, IM-2, IM-3, IM-7
Likewise, other category recommendations are available based on the service.
There are some categories which do not have recommendations related to Cosmos DB such as DevOps Security(DS), Governance and Strategy (GS) and etc..
However, these are only to guide you towards compliance as Microsoft specially mentions by adopting this you do not become compliant.
So how shall we start? Pick the list of resources you have, go one by one and see what are missing. Then plan how you can make them fit into the guidelines. Easy as that.

This comment has been removed by a blog administrator.
ReplyDeleteI read a article under the same title some time ago, but this articles quality is much, much better. How you do this.. Log4j
ReplyDeleteGreat Information sharing .. I am very happy to read this article .. thanks for giving us go through info.Fantastic nice. I appreciate this post. security company
ReplyDeleteI haven’t any word to appreciate this post.....Really i am impressed from this post....the person who create this post it was a great human..thanks for shared this with us. best security company
ReplyDeleteI value the article. Really thank you! Much obliged.
ReplyDeletesecurity guard company in phnom penh
very interesting keep posting. cctv surveillance
ReplyDeleteThe information in the post you posted here is useful because it contains some of the best information available. Thanks for sharing it. Keep up the good work Bug Sweeping Company.
ReplyDeleteThe context of this content is really good. Thank you for sharing this type of awareness with us. In this article, you shared much informative knowledge on multiplication activities. Take look at this tooToronto Construction Security Guard Service . Thanks!
ReplyDeleteI really appreciate your work which you have shared here about The article you have shared here is very informative and the points you have mentioned are very helpful. Thank you so much.Diseñador de calendarios Roses
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteYou are doing a great job by writing such an informative article. Interesting at the same time. Also check this out SIA Security Guarding Top Up Only £99. Thank you.
ReplyDeleteYou've written an excellent post, and you've shared it with us. Your article provided me with some unique and useful knowledge. I appreciate you sharing this text with us. Security Companies in Bakersfield CA
ReplyDeleteEnjoyed every bit of your blog post. Really looking forward to read more. Fantastic.
ReplyDeletedata archiving
Really appreciate you sharing this post. Really thank you! Want more. hire security company
ReplyDeleteSecurity essential
ReplyDelete